For me, it has been clear since Windows 8 that Windows in the Home Edition can only handle Bitlocker with tricks. So especially with encryption, because decryption was never a problem. In Günter Born’s blog about a post on Bitlocker in Windows 10/11, my perception of the world was shattered in this regard.
In disbelief, I tried it out on my father-in-law’s PC (he is the only one in my circle of friends who bought a new PC in the last few years). And indeed, his HP PC is affected and encrypted.
The problem
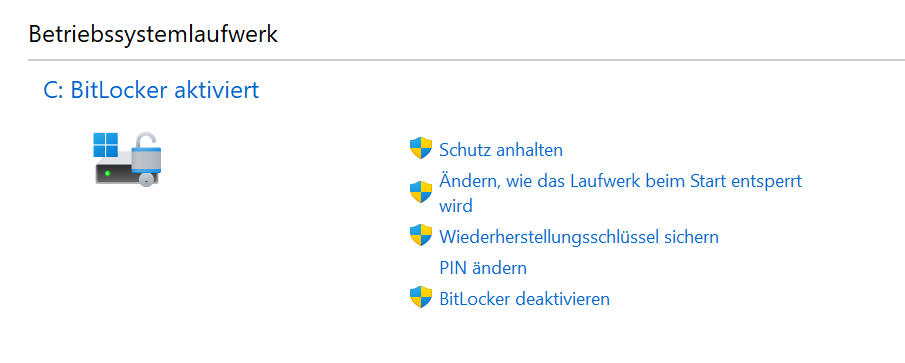
The fact is that the PC is encrypted with Bitlocker by default and the operating system in the Home Edition does not even bring the Bitlocker management console. I could have seen that in Explorer, but I didn’t.
To back up the recovery key, I also just searched for the term Bitlocker and didn’t find anything. So I resorted to manage-bde. This command line operation of Bitlocker works reliably and has served me well in the past. For administrators of corporate networks that disallow the use of the Bitlocker management console, it should be noted that manage-bde often works anyway.
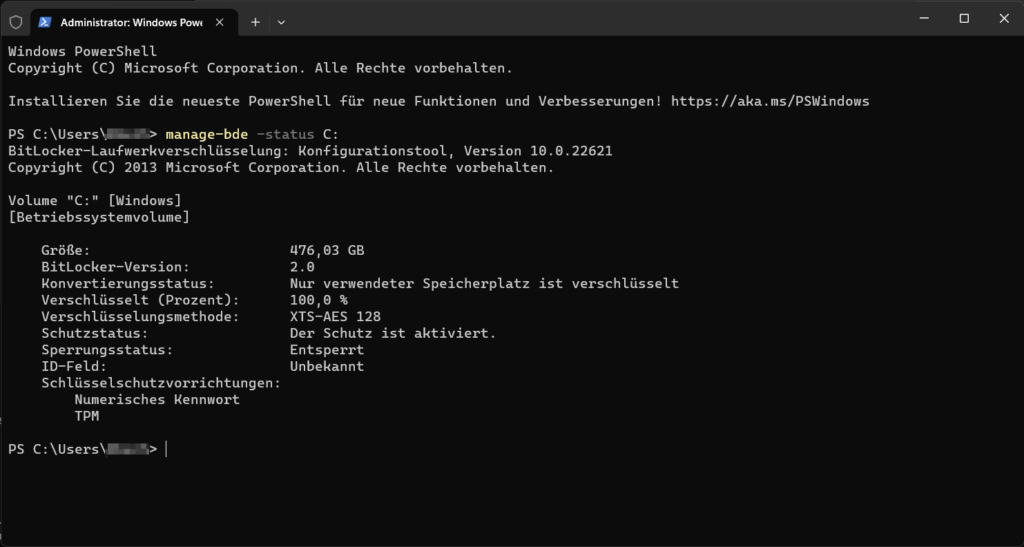
As an administrator, manage-bde can be started in the terminal with
manage-bde -protectors -get C: > C:\BitKey.txt
you can simply save the existing recovery key and it is no longer a problem.
Background
Shortly after that I listened to episode 46.8 “Encrypting data securely” of the c’t uplink podcast (with plenty of delay after publication). This also covers the topic and discusses details and justifications for Microsoft’s approach.
Important to me:
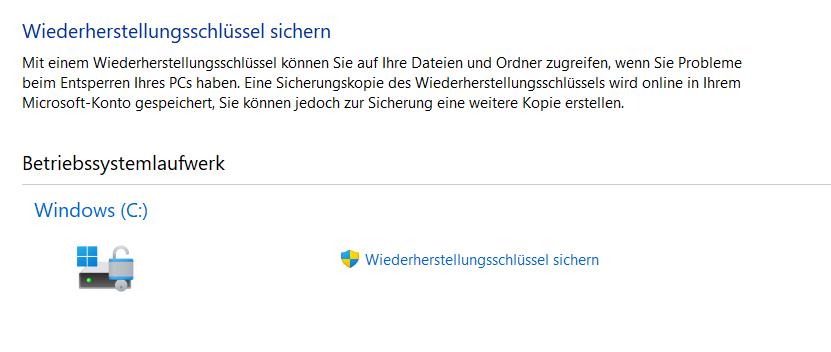
- Encryption is not performed until the recovery key is backed up to the Microsoft account.
- The recovery key can be viewed at https://account.microsoft.com/devices/recoverykey.
- There is at least one option with device encryption to get the recovery key in the settings as well.
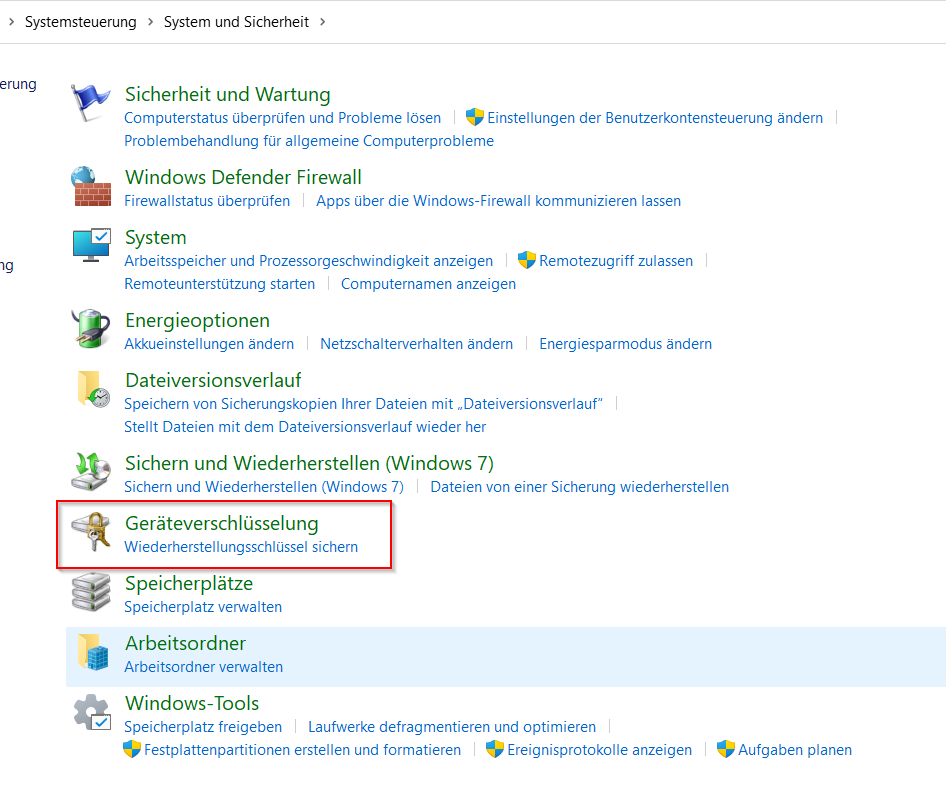
The device encryption of the Home Edition is of course very limited:
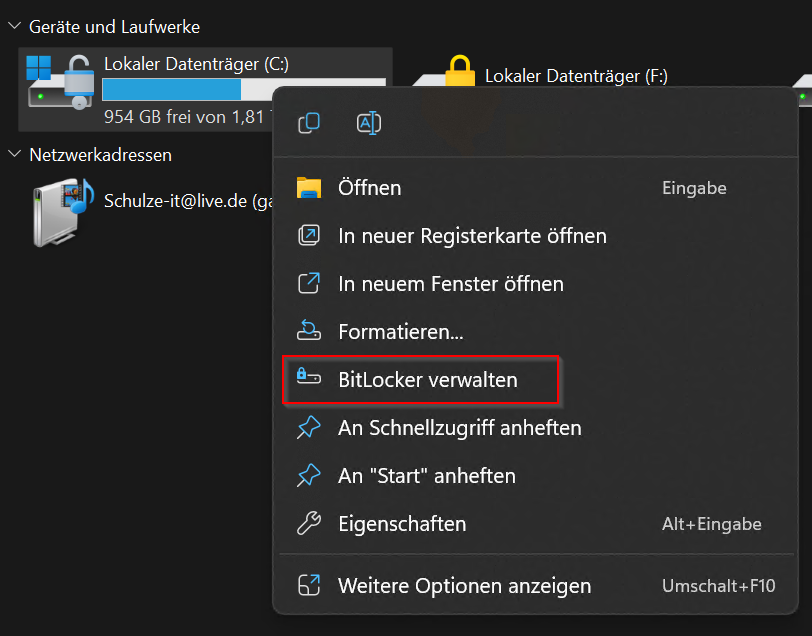
In the Pro edition, it’s all a bit more obvious:
Opinion
Nevertheless, I consider Microsoft’s approach to be problematic. An explicit hint is probably not intended, in order not to confuse the users. But if something goes wrong (Murphy and so on) and Windows wants the recovery key, the problems start. I know some PC users for whom this would lead to a total loss, because they don’t know their Microsoft password/account, as they have been logging on to the PC only with the PIN for years. And then if all the data (e.g. password manager) was only on the PC or even in OneDrive, it becomes difficult. A backup would be helpful, but has generally not yet been implemented.
Since it only affects newer OEM PCs and the average PC in my administration area is older than ten years, I don’t have to take much action. I have yet to find out if it would also be possible to manually start device encryption on older devices. With the end of support for Windows 10, that will probably change.
Also, I’m surprised that despite the claim that it’s for user security, only limited device encryption is available. With a complete Bitlocker, users could also encrypt removable media, etc. and be even more secure.
PIN
I am also a big fan of PIN entry before Windows startup. Even in the Pro edition, you can’t set this up without gpedit.msc or manage-bde. In the Home edition, I honestly haven’t tried it yet, but it would be interesting to see if a PIN can be added in device encryption.
And then there are the devices that don’t have a pre-boot keyboard (some Surface devices) and therefore need a more sophiosticated solution to enforce a PIN.
Summary
Basically, I like Bitlocker and think it is good that it is now possible on (OEM) devices with the Home edition of Windows. But this silent introduction through the backdoor may be good to not overload users, but it is also a source of errors.
In any case, I now have another item on the list that I will pay attention to when setting up third-party PCs.
Translated with www.DeepL.com/Translator (free version)