I already wrote this article partly on the 30th birthday of SMS in early December 2022, but then it had lost relevance for me. Instead, ChatGPT has written a post , but it goes in a different direction.
In regard to the current discussion about the deactivation of SMS as a second factor for non-subscribers of Twitter, I would like to take up the topic again after all.
The situation with Twitter
Since I am not a friend of SMS for MFA, I am not directly affected by this change. In general, I have the impression that the people around me either use MFA only when they have to and then as simply as possible (meaning they like it via SMS) or are so security-conscious that they prefer TOTP. Since there is no enforcement (not even a friendly encouragement) to use MFA on Twitter, it probably only affects a minority. On DarkReading I read interesting figures: 2.4% of users use MFA and >70% of them use SMS.
In my article on MFA from April 2022, SMS is already at level 5 of 8 in Daniel Miessler’s chart. SMS can be seen as an additional protection (if the password is not weaker, reused or worse protected). Therefore, the SMS also has its justification for existence for MFA and can have a positive effect. Not every attacker is willing or able to perform sim-swapping.
But there are also grown environments: If nothing other than SMS was offered in the past, it is enabled once. A change in authentication procedures is always inconvenient and often postponed. Admittedly, I also still have a few such accounts.
Back to Twitter: In general, I wonder what this step is all about. The SMS sent to bots probably cost too much money and that is only acceptable for paying Blue customers ( regardless of whether it’s a bot or not). In general, I would find it interesting to know more details about whether bots are more likely to use MFA than humans. I wouldn’t have expected this to be a problem unless MFA is enforced. Also, the figure of 2.4% (above from DarkReading) does not point to bots for me, as the proportion would be significantly higher otherwise.
From the point of view of the security and attractiveness of Twitter Blue, it would be logical to say that even the extended security with TOTP or FIDO2 would only be possible against payment, wouldn’t it?
I don’t want to complain, because I too only pay Twitter with data/advertising instead of money. I find the discussion that has occurred quite notable.
I think the cases where Twitter is now about to migrate from SMS to TOTP and this will provide the incentive for more secure MFA can be counted on one hand. Probably even more people will deactivate MFA rather than migrate the MFA process.
As a bot, I would have preferred TOTP before, but I don’t run a botnet and can only make educated guesses.
Mandatory SMS
Vice versa, there are also services that continue to offer only SMS as an option for MFA or even enforce this. If not for MFA, then for user identification during registration (with the same security issues).
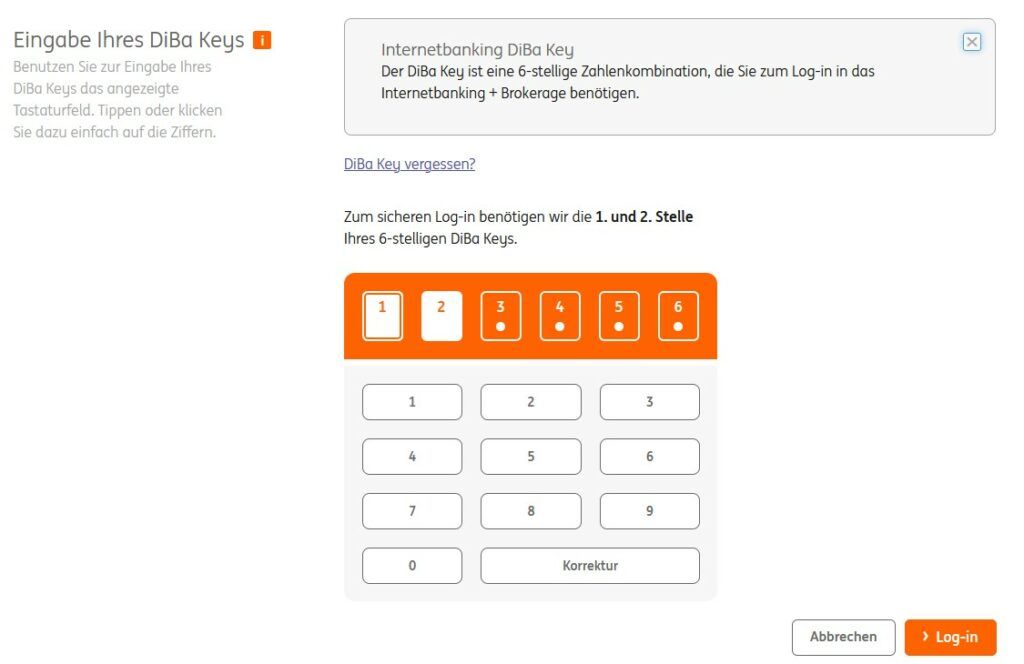
Since the end of 2022, it is mainly ING that has been annoying me. My three accounts are also quite different. For all accounts, in addition to the access number and PIN, there is also the DiBa Key as a quasi second PIN (2x knowledge).
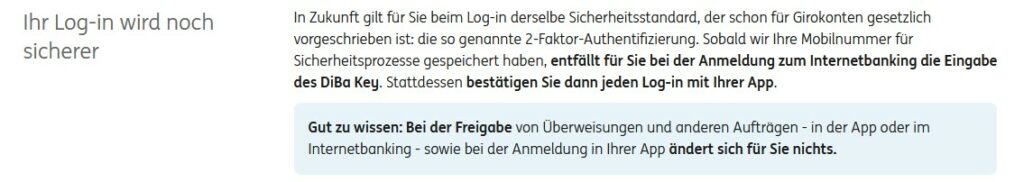
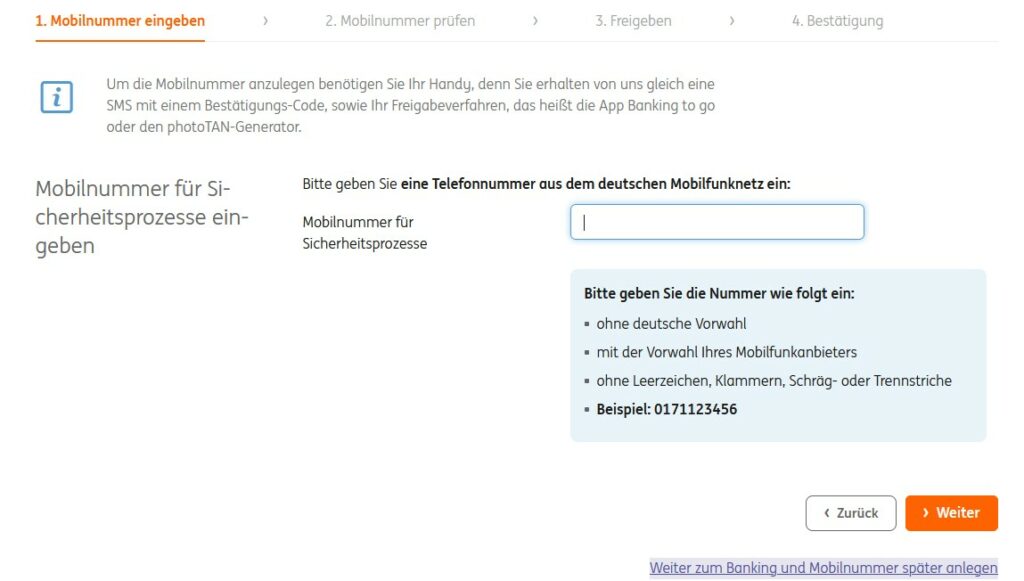
However, one of the accounts wants me to enter my “mobile number for security processes”. This query comes up every time I log in and that’s two more clicks each time. I’m curious how long I can keep clicking away this message.
From my point of view, a secure second factor would be preferable. I also find it highly problematic that the banks now also use telephone numbers and email addresses, because that makes the phishing possibilities more plausible for attackers. During my awareness trainings more than 10 years ago, I could still confidently say that all SMS and e-mails from the bank can be ignored because they don’t contact you that way. Unfortunately, those days are over.
With the second account, I was unfortunately unable to avoid giving the telephone number due to a change in the accesses. Fortunately, the third account has so far not been interested in the telephone number.
One point about using SMS as a backup for access should not be underestimated: There are enough services that you might only use very rarely. I have not used Twitter at all for many years in between. If the phone number changes, you might have a problem. I have stored in my KeePass which telephone number I have entered where, especially as I used to change numbers more often. I think there are enough cases where this goes wrong – especially if the phone number was not entered voluntarily/consciously and only quickly during registration.
I seem to recall that there have also been cases where phone numbers that were only deposited for security purposes have been misused for other purposes. A quick search reveals that it was even Twitter ?.
SMS security
I also only use SMS very rarely. Either as a reminder for doctor’s appointments or for a few people who use WhatsApp as their only messenger otherwise. However, a few conversations have already been switched to RCS.
I have not noticed any cases where the SMS sent automatically during registration or for MFA purposes have been replaced by RCS. Why not? Twilio, for example, has already been able to use RCS for five years, but probably at different prices than SMS. But if I now had to pay for it at Twitter Blue, I would probably be able to expect that, wouldn’t I?
I find it particularly problematic when SMS is used as a way to recover a lost password.
Other alternatives
Apart from TOTP and FIDO2, I can think of a few services that do things differently. Some banks have special apps, some even have several apps. Thanks to PSD2.
I have already announced that I prefer e-mail over SMS. I find the implementation of Bitcoin.de particularly good, as the emails are even PGP-encrypted and -signed.
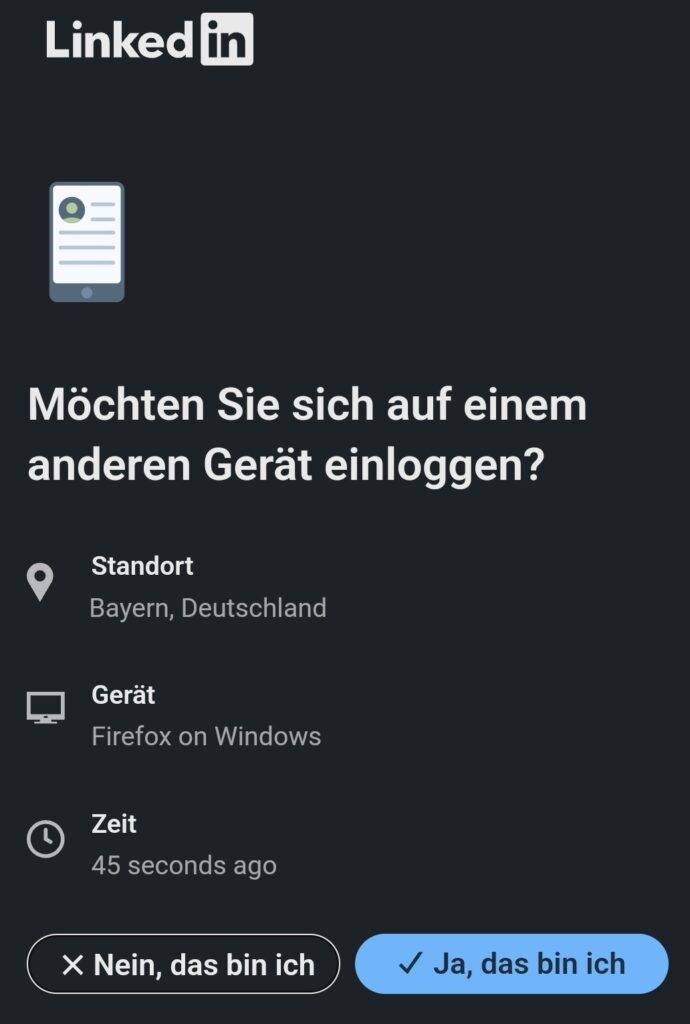
At LinkedIn, I noticed for the first time this week that, in addition to TOTP, it is also possible to authorise logins through the app.
At first sight, I can’t stop this at all and it’s even preferred over TOTP.
Even Telegram has recently added an additional password for two-step confirmation, but then also wants to collect the email address right away.
Or Lidl always offers me the option of using SMS or email. This way, an attacker can choose the easier target. Unfortunately, you have to provide a phone number.
When GTA V was available for free in the Epic Store, I remember that logging into the store didn’t work for a very long time because the e-mails were only sent or arrived after the validity of the code had expired. This can also happen with SMS.
But Xing also screwed up MFA somehow. Since I set up TOTP, the Android app wants a new login with email, password and TOTP code every time I access it. That’s very annoying, but since then I’ve been using Xing much less.
Summary
In summary, it can be said that SMS as a second factor for logging in is quite convenient. It can be more secure than a pure password, but it is the weakest of all MFA options.
I can’t quite understand Twitter’s move to deactivate SMS MFA for non-Blue subscribers. As an optimist, I see this as an opportunity to improve distribution for TOTP, FIDO2, PassKeys etc.
However, I miss the possibility of being informed by e-mail or in the screen after login about the last successful and failed login attempts for many login processes.