The topic MFA, was already here more often in focus. After I ordered my Nitrokey 3C NFC in June 2022, it was delivered on World Password Day on May 4th 2023. The delivery delays were at least transparently presented in Nitrokey’s blog.
So far
In the past I have used TOTP a lot. Especially after the article MFA – More Fun in Authentication or Most Faulty Authentication? I became more persistent. The very long list in my Authenticator App and especially different codes for the same service (e.g. several differently privileged accesses for AWS or for my blog) always made it a bit annoying to find and type the right code. Maybe changing the Authenticator app would have made a difference, but that’s still on the to-do list.
Terms
According to ChatGPT, the following term distinctions are relevant:
- WebAuthn: WebAuthn stands for “Web Authentication” and is an open web standard developed by the World Wide Web Consortium (W3C). It enables strong, secure, and user-friendly authentication on the web without the need for passwords. With WebAuthn, users can verify their identity by using various authentication methods such as biometric data (e.g., fingerprints) or security keys (e.g., USB security keys).
- FIDO2: FIDO2 is a security standard developed by the FIDO (Fast Identity Online) Alliance. FIDO2 is based on WebAuthn and encompasses both WebAuthn and CTAP (Client to Authenticator Protocol). CTAP allows communication between a web browser and an external authentication device, such as a security key. FIDO2 extends support for strong, passwordless authentication methods across different platforms and provides increased security compared to traditional password-based methods.
- Passkey: The term Passkey generally refers to a unique code or combination of characters used for authentication or authorization of users. A passkey can be a password, PIN, or passcode. In the context of security keys or wireless devices, a passkey can be used as a security mechanism to establish a secure connection between devices. A passkey can also be employed in two-factor authentication to enhance security during the login process.
In summary, WebAuthn is an open web standard that enables authentication on the web, while FIDO2 is a security standard built on WebAuthn, supporting passwordless authentication across various platforms. Passkey is a general term for a unique code or combination of characters that can be used for authentication or authorization and can also be relevant in the context of security keys.
I always try to use the terms correctly in the following. By the way, Heise has published a good article about this.
First impression
At first look, the Nitrokey makes a robust impression. The USB-C plug sits relatively tight when plugged in, but I prefer that to being too loose. A protective cap would give me a better feel, but it is not necessary. I put an adapter for USB-C to USB-A on it – you can always use that.
Unfortunately, the Nitrokey cannot be connected to my smartphone via USB-C without removing the case at the bottom. However, this is not due to the Nitrokey, but to the case. Good for that I have (theoretically) ordered the version with NFC.
Initial setup and general principle
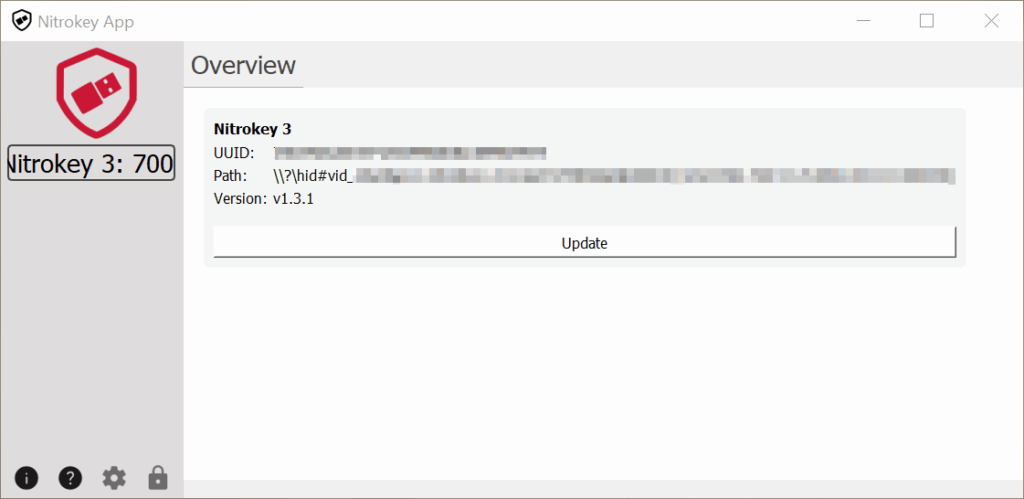
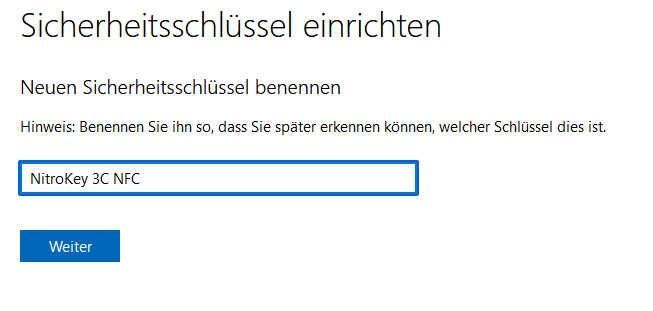
Basically, the security stick is ready to go right out of the box. I did install the Nitrokey App 2, but only to find out that the latest firmware was already installed. There are some helpful links www.nitrokey.com/start and the guide for Windows, but you don’t need to read much before using it.
When first setting up with a web service, the operating system, or browser, detects that a PIN has not yet been set and prompts the user to create one.
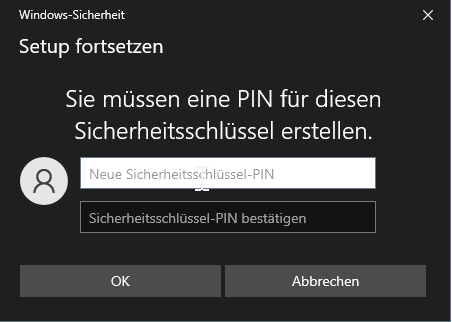
The process is also otherwise controlled by the browser or operating system. During setup, the user selects the security key option, enters the PIN, and physically confirms that on the security key by touching it. I missed the touch field on my YubiKey the first time, but it’s even better without it.
Basically it’s the same when using it, except that the security key is then shown directly as a login option.
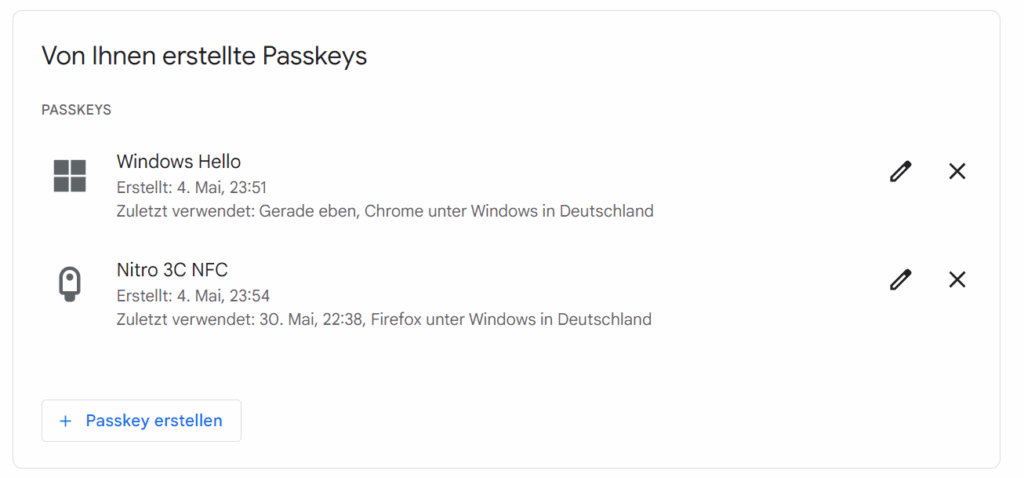
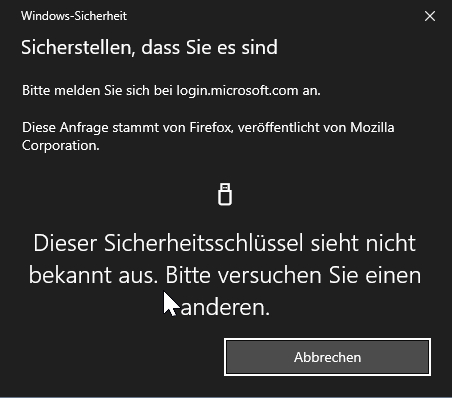
I just have to be careful, because Windows Hello is also stored as Passkey and you see the security key as a second option. At the latest after the hint of the wrong PIN it is noticeable.
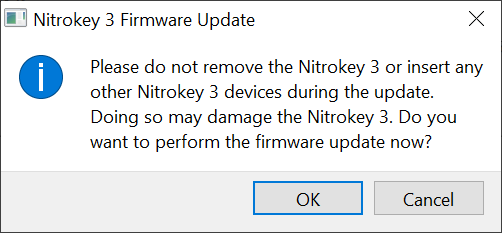
Meanwhile, there is the update to firmware 1.5.0, but the update with the Nitrokey App 2 is trivial. The only thing that caused a brief moment of confusion was that the app still displays the old firmware version after the update and has to be restarted itself.
Test with Google
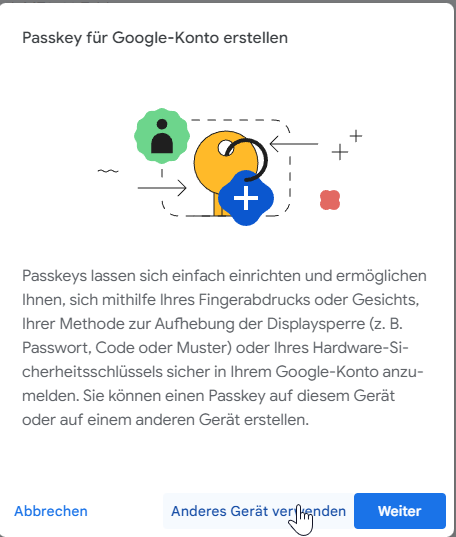
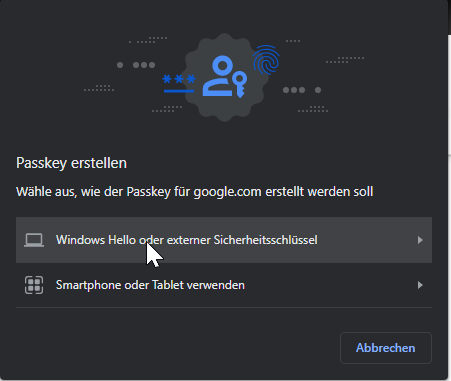
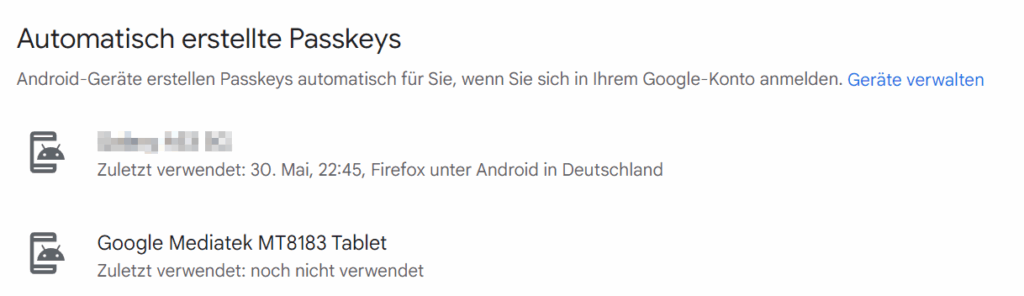
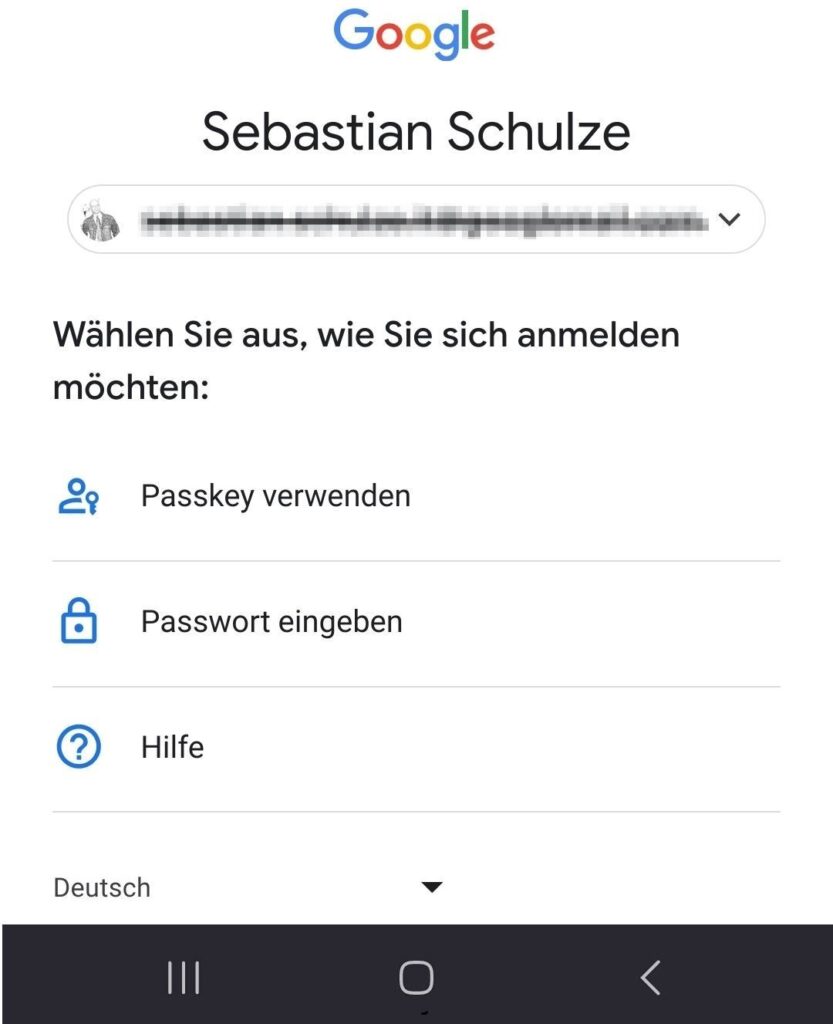
Since Google has advertised the support of Passkeys at the beginning of May and is therefore predestined for the first test. Also, I consider the Google account to be one of the most worth protecting. The setup is very intuitive.
Google has the feature that every logged-in Android device is already stored as a passkey and a new login on one of the devices has to be confirmed (I didn’t notice ChromeOS).
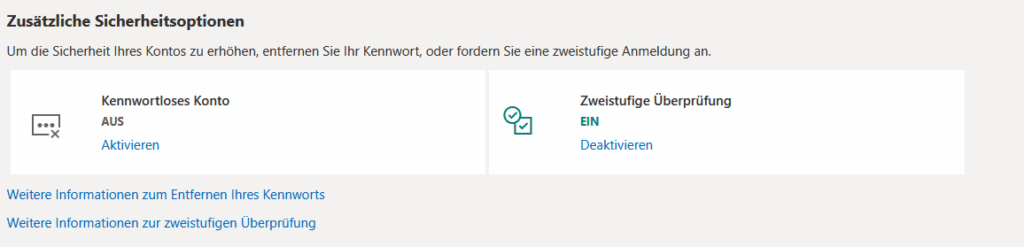
In general, Google has a very long list of possible second factors or for account recovery after forgotten password (SMS, other mail address, recovery codes, etc.). Here it may be worth to remove previous old methods (I removed my phone number).
Google offers that the user can decide whether a password is required in addition to the passkey or not. In either case, however, I have to provide the email address for identification as the first step. WebAuthn could also eliminate the need for this step.
Test with Microsoft
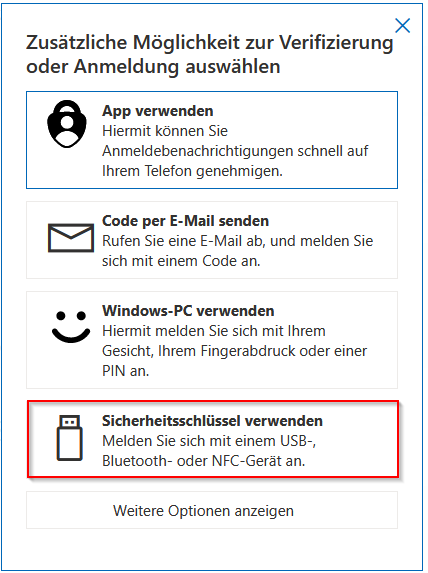
Microsoft has already integrated a passkey solution into Windows for a long time with Hello and the use of the PIN of the Windows account.
Microsoft differentiates between USB and NFC security keys. Using NFC is not possible with my laptop, so I used USB. Let’s see if NFC can still be used later.
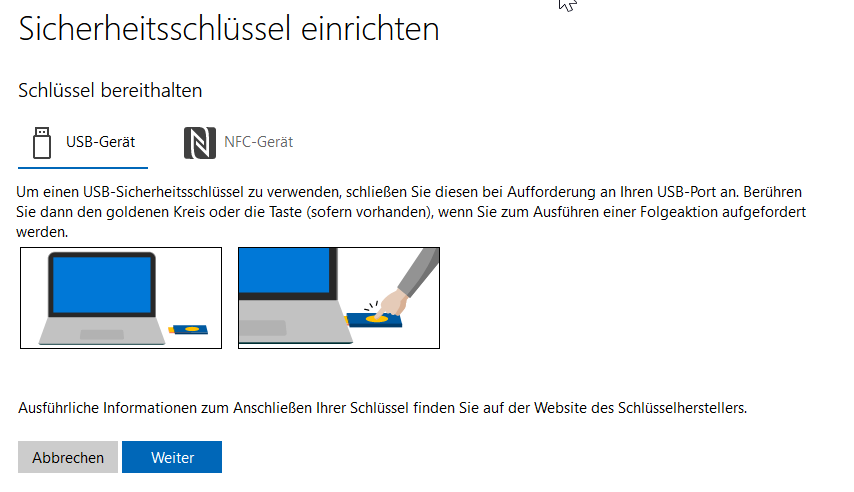
As with Google, there are many hints and warnings in the Authenticator app when setting up security keys – very well-executed.
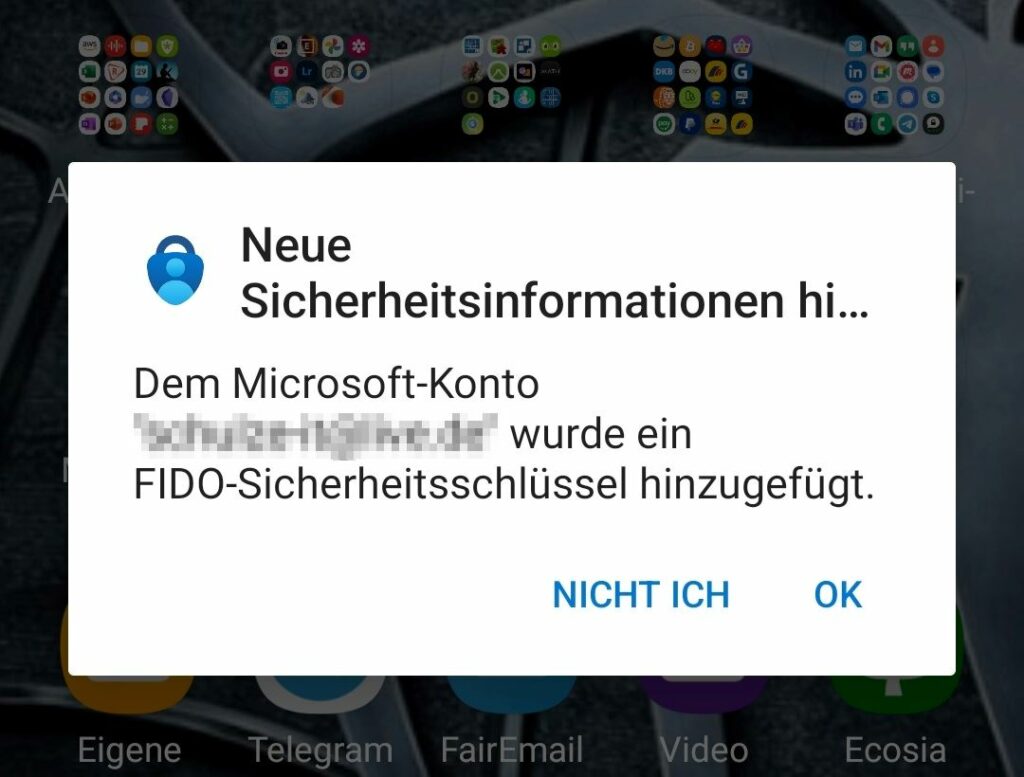
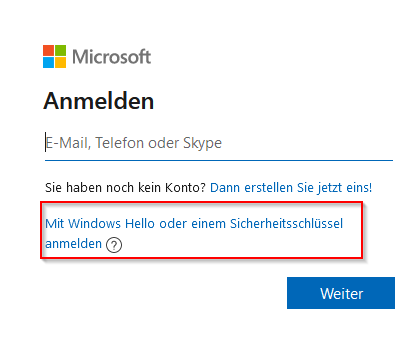
From my perspective, Microsoft does something right that I missed with Google: WebAuthn allows logging in without specifying the account (e.g., the e-mail address), and that’s exactly what happens. When I log in, I specify that I want to use the security key instead of the email and the usual passkey window appears, offering me Hello or the FIDOI2 security key. That’s the way I had imagined it. With Google, this option came only after identification.
Accordingly, of course, an error message comes if the security key is not registered.
A passwordless login is also possible here.
NFC on Android
Testing the NFC function on the smartphone was not trivial and so far unsuccessful. Both with Firefox and Chrome I had no success. On Android, Google would rather use the passkey of the Google account on the Android device and requests the fingerprint directly.
On another Android device (with a different Google account), it doesn’t find an associated passkey at all (because the device’s Google account is different from the one you want to log in with) and doesn’t even bother asking for the security key.
Microsoft also does not offer this login at all on my Android device and no login is possible on the Android device.
In addition to Firefox on Android, I also tried Chrome. With the Google account, logging into Chrome was pointless since I’m already logged in there via the OS.
So all in all, I had no success. Also, using it via USB instead of NFC was not possible at all. The security key is at least charged.
Test on the iPhone
To make a long story short: Since Apple’s NFC interface is closed and the USB-C to Lightning connectors also work rather poorly, the main advantage is that you save yourself the time to try it out in the first place. However, the result is the same.
I suspect passkeys based on the OS will become more common on mobile devices than FIDO2 security keys. Too bad really.
AWS
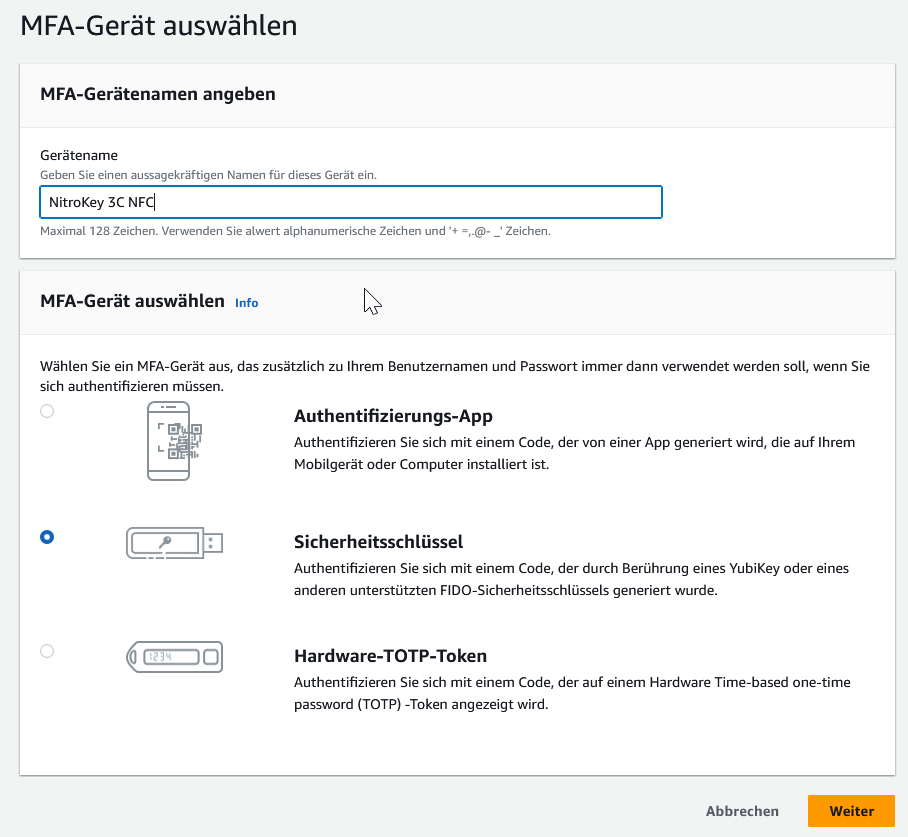
In AWS, logging in the root user is unfortunately always a pain (on purpose?). Since I have multiple accounts in AWS for different services with different privileges, a FIDO2 security key would be a good thing in theory.
In reality, the login looks like this after that:
- Email address
- Captcha code
- Password
- Security key from the FIDO2 stick OR the code from the TOTP app.
This is a bit more convenient, but I would still like to do away with the password or at least the captcha.
Test in the field
Full of energy I wanted to secure some services with FIDO2 or WebAuthn, but no luck. Especially services that I would also want to use on the business PC, because a dual use makes sense, would be so ideal. To use these services not only secured with a second factor, but without a password (which somehow has to come from my KeePassXC to the work PC (or even without specifying the login name, or the email address) would be perfect. Unfortunately, neither LinkedIn nor Xing offer this yet.
My MFA plugin for WordPress can’t handle WebAuthn yet, but I don’t install additional plugins so lightly.
Further plans
The protection of the KeePassXC container is still planned, but did not work ad hoc. On the part of NitroKey this is possible in the current firmware. Soon I still want to test the function for PGP.
Summary
The main problem of WebAuthn and FIDO2 is from my point of view still the insufficient propagation. On https://www.dongleauth.com/ or https://passkeys.directory/ there are nice overviews. In my opinion passkeys could be more successful in this regard.
I prefer a separate security key in hardware and a solution independent of an ecosystem. The passkey solution in the operating system is of course more convenient, but only on one device. The planned synchronizations are more of a new vulnerability than a solution for me.
Translated with www.DeepL.com/Translator (free version)